Software development
What Is Alm? Application Lifecycle Management Defined
In essence, ALM serves as the backbone of contemporary software improvement practices. By fostering collaboration, enhancing security, and supporting swift iterations, ALM ensures that organizations can navigate the complexities of at present’s software ecosystem effectively. On the other hand, Utility Lifecycle Administration (ALM) encompasses a broader spectrum. Whereas it actually includes the development process, ALM spans the complete lifetime of an utility — from inception to retirement. An ALM technique integrates numerous phases of SDLC and extends past, addressing the appliance’s maintenance, optimization, and eventual phase-out. ALM emphasizes department coordination, making certain seamless improvement, maintenance, and governance integration.
What Are The Benefits Of Alm Compared To Traditional Utility Development?
This stage contains identifying current issues, planning, design, building, testing, deploying, and so forth. To overcome such challenges, organizations must implement ALM options that present visibility across varied departments and insights that group members with totally different fields of expertise can perceive. ALM options integrate present tools and platforms to provide customers a centralized view of knowledge. The instruments and methods used in ALM create a constant project view for all teams. Everyone knows the work that has been done up to now and the duties that also have to be picked up.
The major function of ALM is to oversee all of the tasks concerned within the alm full form software program development and to make sure that every thing runs as easily and successfully as potential. It is usually manifested in a set of instruments or a software program suite that eases communication and collaboration among different stakeholders, thus guaranteeing that software program initiatives are delivered on time and inside budget. Furthermore, it helps to mitigate dangers by making it simple to track progress, determine potential issues early, and reply shortly to modifications or issues.
When your ALM technique is harmonized with other enterprise processes, it results in more cohesive software improvement, improved product quality, and elevated buyer satisfaction. In right now’s quickly evolving tech landscape, Application Lifecycle Administration (ALM) holds extra significance than ever before. Modern software growth practices like DevSecOps and Agile methodologies necessitate a extra built-in and iterative strategy to application administration. A mix of handbook evaluations and automatic check suites comb via the software, identifying bugs, efficiency bottlenecks, and inconsistencies. From guaranteeing features work as intended to guaranteeing responsiveness underneath peak masses, this stage is devoted to refining the software to satisfy or exceed the quality benchmarks. Software lifecycle administration (ALM) is the people, instruments, and processes that handle the life cycle of an utility from conception to finish of life.
- For example, a linear projection followed by SoftMax activation is commonly utilized in language modeling.
- In the testing part, the testers must confirm that the application is complying with the necessities outlined in the preliminary steps of the method.
- The software program improvement lifecycle (SDLC) is a systematic methodology that you can use to produce quality software affordably.
- CD permits teams to make updates and correct errors extra quickly, which reduces utility downtime.
It helps in defining project requirements, setting project milestones, assigning duties, monitoring progress, and resolving issues. ALM ensures that the project stays on schedule and inside finances, whereas also assembly the standard requirements and customer expectations. In conclusion, ALM performs an important position in enhancing group collaboration by offering a centralized platform, real-time visibility, seamless integration, and assist for agile practices. By leveraging ALM instruments and practices, groups can streamline communication, foster collaboration, and deliver software program projects more effectively, finally leading to improved productivity and buyer satisfaction. ALM also emphasizes the significance of collaboration and communication between totally different teams and stakeholders concerned in the software program development process. By offering a centralized platform for managing and tracking software program growth activities, ALM allows groups to work more efficiently, reduce errors, and enhance overall software program high quality.

Use Case Scenario Of Alm From A Project Leader Perspective
As advanced, smart, and connected products turn into the norm, manufacturers should deal with increasingly stringent laws. Manufacturers must additionally meet rising buyer expectations and overcome unpredictable provide… Through my writings, I aspire to empower you with information, enabling you to make informed choices in the https://www.globalcloudteam.com/ digital world.
This stage consists of planning for a way updates will be managed and establishing monitoring techniques to track the application’s performance. Deployment isn’t merely “going stay” – it requires careful planning to make sure a easy transition for customers Digital Logistics Solutions and minimal disruption to enterprise operations. Also, it’s price pointing out that, even today, many groups naturally apply sure ALM aspects — along with the aforementioned methodologies — within the improvement process, with out actually knowing it. In other words, they haven’t set the trail for an outlined course of round these concepts; but, that’s precisely what they want to do, to streamline the event course of. Certainly, figuring out the entire ALM course of, with its particular phases — and faithfully following alongside, step by step — will increase both their productiveness and the standard of the software program they’re creating. In a method, the very nature of application lifecycle administration is such that it dictates the adoption of Agile, Lean, and DevOps growth approaches.

LLMs can generate context-aware and coherent textual content, making them useful for duties such as writing essays, inventive tales, promoting copy, and even formal documents—all with a deep understanding of context and tone. LLMs can help personalize experiences by understanding consumer preferences and providing tailored suggestions. Traditional NLP used rule-based techniques and shallow machine learning fashions. Extra fashionable NLP uses deep studying and transformer fashions (like LLMs) which have dramatically improved the accuracy and efficiency of these methods. In contrast, an LLM is a a lot bigger and more highly effective language mannequin with billions to trillions of parameters, trained on huge datasets. They are trained on monumental datasets with text from the net, books, analysis papers, and extra, enabling them to study a extensive variety of language patterns and world data.
Test-driven improvement (TDD) and steady integration (CI) are two important practices in software development that goal to improve code quality and efficiency. ALM is often used interchangeably with other associated phrases, corresponding to SDLC (Software Growth Lifecycle) or EALM (Enterprise Utility Lifecycle Management). Whereas there could additionally be subtle variations of their definitions, these references are typically used to describe the identical concept of managing the lifecycle of software program functions. Throughout this stage, developers write the code and build the application based on the requirements. While that is primarily technical work, enterprise groups stay involved to ensure the app remains aligned with business goals.

Enterprise Expertise To Help Alm
ALM is a key course of in efficient and efficient software program growth aiming to make sure high quality and scale back time to market. ALM involves DevOps and enterprise groups working collectively for the whole application lifecycle to deploy and ship functioning applications that meet enterprise aims. ALM instruments streamline the creation of functions through an outlined methodology meant to create quality products. Software lifecycle management tools assist IT operations automate processes and workflows that result in faster deployment and higher upkeep all through the appliance lifecycle. When referring to software program development, ALM is a complete strategy that covers the whole lifecycle of an application. It consists of processes related to requirements management, project management, model control, construct management, testing, deployment, and monitoring.
However, the method does not end right here; for the appliance to stay healthy and sturdy, we have to monitor and maintain it typically. Lastly, when the applying not has value for the purchasers, it reaches its end of life. In essence, while SDLC focuses on the “how” of making software program, ALM provides a holistic view, addressing the “how” in addition to the “what” and “why” throughout the applying’s entire lifespan.
Look for a software that features model control, the power for groups to communicate in real time, requirements management features, estimation and project planning, source code management, and take a look at management. In the context of ALM, the identification and prioritization of software requirements serve the purpose of offering a transparent understanding of what the software program ought to accomplish. This process helps to align the expectations of stakeholders and development staff members and ensures that the project stays on track by delivering worth early and continuously.
Still, additionally it is the one where the participation of the testing and improvement teams is usually the bottom. The bank’s high quality assurance team verifies the enterprise case of opening accounts for its mobile banking software. Since the financial institution additionally accepts passports as ID proof, they ask the event group to replace the application to incorporate this data. The staff members determine that they need to full the customer’s consumer story first, then test it completely earlier than starting on the administrator’s requirements. Nonetheless, they know they have to finish both requirements before launching the new product.
Software development
25 Best Software Program Development Instruments Reviewed For 2025
Slack is designed to streamline group communication with real-time messaging, file sharing, and integration capabilities. With Slack, you’ll have the ability to create channels for different tasks or groups, facilitating organized discussions. As the every thing app for work, ClickUp is designed to optimize software improvement and project administration workflows. The most necessary step and problem to tackle is the biases in coaching information. This could perpetuate healthcare disparities such because the underrepresentation of particular demographic teams or the reinforcement of historical biases in knowledge assortment 98. Compounding this issue could be a dataset shift post-deployment the place the model’s operational setting differs from its training surroundings causes a degrade efficiency and compromise generalisability 99.
For occasion, you would possibly use Azure’s AI services to add picture recognition options to your app, enhancing the user expertise. Microsoft Visible Studio begins at $45 per thirty days and provides some free instruments to individuals. This desk compares numerous programs provided by Simplilearn, primarily based on a quantity of key features and details. The desk supplies an overview of the courses’ length, expertise you’ll be taught, extra advantages, amongst different essential factors, to help learners make an informed determination about which course most precisely fits their needs. These search APIs run regionally on all device varieties and offer seamless performance and privateness. JetBrains is a collection of professional-grade IDEs that cater to virtually every programming language and framework out there.
Introducing App Actions On Windows, A Brand New Capability For Developers To Extend Discoverability For Their Apps
- Neural networks in AI are sometimes referred to as “black boxes” as a outcome of their internal workings are complicated and never easily understood.
- Windows ML is the inspiration of our AI platform and is the built-in AI inferencing runtime, providing simplified and efficient mannequin deployment across CPUs, GPUs and NPUs.
- They developed the ENDEAVOUR AI platform, a comprehensive AI system that integrates varied instruments to streamline operations 85.
- If you and your team are developing a Node.js software, Cloud9 offers a pre-configured setting, allowing you to begin out coding immediately without native setup hassles.
Superior Windows Settings permit developers to simply management and personalize their Home Windows expertise. They can access and configure highly effective, superior settings with only a few clicks, all from a central place within Home Windows Settings. These embrace highly effective settings like enabling File Explorer with GitHub version management details.

As developers ourselves, we all know how important and troublesome it’s to make the best determination when deciding on software program. Codenvy is among the finest software program improvement instruments that permits you to code, build, and debug applications instantly in your internet browser. This means you probably can work from anywhere with an internet connection with out installing something on your native machine. Evaluating AI fashions against professional clinicians is crucial to understanding their medical utility and assessing their algorithmic high quality https://www.globalcloudteam.com/ 105. Whereas some AI models obtain expert-level accuracy, a scarcity of rigorous examine design typically results in overestimated efficiency claims.
Following registration procedures, scientific deployment and continuous performance monitoring occur. Lastly, a dedication to bettering the AI ecosystem ensures its adaptability to evolving clinical needs. This evaluation explains the similar old path for new AI tool growth and deployment in healthcare and clinical providers. It concurs with different analysis frameworks 31, 32 (Table 3) and could possibly be extended to include assessments of well being economic advantages 33.
JetBrains is a software growth company that creates instruments with productiveness options and code analysis capabilities for software program builders and project managers. Monday Dev is a product administration software that centralizes the complete product lifecycle and syncs development and collaboration instruments in real-time. It allows users to customise workflows and helps break down silos between R&D, design, and product groups. Below are my detailed summaries of the best software program growth tools that made it onto my shortlist.
AWS Cloud9 additionally makes it simple to collaborate with my team in real time, which enhances productiveness, especially when working on serverless functions. Trello is among the hottest project administration instruments with an intuitive drag-and-drop interface that helps you arrange development duties. It enables you to create a board for a project, add lists to symbolize levels and populate them with playing cards for particular person tasks. It helps a variety of programming languages, has an extensive library of extensions, and offers a easy, lightweight expertise without compromising on powerful options like debugging, “Git integration”, etc…,.
The Way To Make A Cellular Game?
In different words, it might be installed on well-liked operating methods like BSD, Mac OSX, Home Windows, and Linux. Furthermore, the concept of Write Once, Run Anyplace applies to the Apache dev surroundings. You can use ChatGPT to construct smart apps that provide conversational options, like writing help, contextual chatbots, summarization capabilities, and coding assistance. If you might be just a newbie, start with Visual Code editor and Git; also, use some on-line platforms to learn how to get started. The beginning can be hard, but you’ll get familiar with Warehouse Automation them as you utilize them.

This open-source toolkit empowers developers to create sleek, mobile-first websites with ease. Feedbug is a visible feedback device tailored for devs and creators who’re in the means of building and refining their MVPs. Customers can easily leave their enter directly on the display screen in the type of sticky notes, reducing friction and enhancing the suggestions expertise. Popular ones embrace GitHub Copilot (AI coding assistant), Docker (containerization), Postman (API testing), and Jenkins (CI/CD). One of Copilot’s biggest advantages is that it understands the context of your code. If you’re engaged on a Python operate that processes user enter, Copilot suggests relevant code snippets based mostly on best practices.
It eliminates the necessity to move from one device to another when constructing software program. Consequently, I appeared out for instruments that might be integrated with a extensive range of software program growth applications and productiveness tools. Apache NetBeans offers a code surroundings and good instruments for building purposes in a number of languages. You can use the easy overviews of every device beneath to understand how each device stands out from different software growth instruments. They generate code, debug help, model control, and project management. This weblog will discuss how to build a crypto wallet one of many two primary aspects of Software Program development tools.
Over the past yr, we’ve spent time listening to developers, studying what they value most, and where we have opportunities to continue to make Home Windows a fair higher dev box, significantly on this age of AI growth. That suggestions has formed how we think about the Windows developer platform and the updates we’re introducing at present. This highly effective chat and messaging API platform allows you to construct participating in-app communication options without breaking a sweat. Axure RP is a powerhouse for creating interactive prototypes and specifications.
Software development
Web Type Spam: What It’s And The Means To Stop It Stop Net Spam
Spam bots usually exploit open-ended fields to inject undesirable textual content or hyperlinks. Validations like requiring an “@” in e-mail protect email address on website from spam fields also can assist display screen out nonsensical submissions. Detecting webspam requires superior algorithms, machine learning methods, and cautious evaluation of internet web page content material and behavior.
Hyperlink Manipulation
Under are actionable methods categorized into content material, technical, backlink, person expertise, and audit enhancements to enhance your site’s overall quality. The strategy manipulates search algorithms, leading to a poor consumer expertise. It’s necessary to create real pages that truly satisfy the visitor’s query somewhat than funneling them deceitfully.
Prevent Spam Utilizing An Anti-spam Plugin
Bots typically fill out and submit forms almost instantly, whereas actual customers take more time. You can measure this by starting a timer when somebody clicks into the shape and stopping it when the form is submitted. Preventing spam is important for preserving your web site operating easily, maintaining web site efficiency, and protecting your popularity.
When you see individuals attempting to access your protected areas a quantity of times knowing their IP so you can block them can be sturdy protection. Some CAPTCHA methods have been hacked, nevertheless it’s nonetheless an efficient block. The drawback with CAPTCHAs is that they can be very difficult for individuals to read. ReCAPTCHA contains an audible version for blind people, but many people don’t realize they will listen to something and get via.
Web Site homeowners can use instruments like reCAPTCHA, honeypots, and IP blocking to stop most spam bots from doing hurt before they can. The only thing that matters if you use this anti-spam strategy is that you just make the query simple sufficient for folks to truly reply. And make certain, if you have a worldwide viewers, translate your varieties into different languages to help encourage kind submissions. One Other technique you must use to deter type spam is to create a kind subject that asks website guests a question that they need to answer appropriately.
This approach goals to leverage present content for better search visibility with out adding originality. Overloading pages with repetitive words disrupts pure flow and may trigger penalties from search engines. Hacked content is any unauthorized materials added to a website as a outcome of security weaknesses. This content material not solely compromises person safety but in addition disrupts search outcomes and may even set up dangerous software program on visitors’ gadgets, severely impacting a site’s reputation. Spammy websites and pages that passed Google’s algorithm are handled by Google’s Webspam team. The staff does guide content material and link critiques and can impose a handbook penalty on a website or its portion.
One thing that is always necessary to recollect is that in most cases no one signal nor strategy is taken into account definitive. This, for these Data as a Product of us taking part in good, means there is a less of a chance of a false constructive. Ninja Forms also uses a Honeypot, which is installed by default on the plugin.
Use A Device Like Akismet To Scan And Delete Spam Submissions
There is no single resolution that may fully protect users from receiving spam, but fortunately there are some steps you’ll have the ability to take to stop being scammed. We all obtain messages from unknown senders once in a while. Whether Or Not it’s the doctor’s office, a job recruiter, or even a message from a long-lost family member, it’s sure to occur sooner or later. But be weary as a result of, more often than not, spam can also be dispatched from an unknown sender.
- Google Analytics is a free internet service that gives comprehensive statistics and analytical tools for search engine optimization and advertising purposes.
- Now we’re launching an initiative to further crack down on spammy content.
- We proceed to reinforce Rights Manager to assist creators defend their original content material.
- Spam is a type of unsolicited communication that is sent to a lot of recipients.
- An important voice in the net spam area is that of search engine optimizers (SEOs), such as web optimization Inc. () or Bruce Clay ().
- Sadly, email spam is likely considered one of the most common forms of spam available on the market, however actually not the only one.
Adhering to the above is one of the best ways to ensure that you recover from most penalties or devaluations. Slowly you might even see your web site begin to get well as Google shifts from viewing you as a spammy net writer worthy of demotion, to being an experience in your field worthy of promotion. These skinny affiliate pages don’t offer customers any priceless or distinct info, and sometimes serve as mere conduits to generate affiliate revenue with out contributing unique insights.

High Quality affiliate content material provides context, evaluations, or comparisons to help customers make higher decisions. With Out such additions, affiliate pages fail to serve their audience effectively. Thin affiliation refers to affiliate pages that provide generic product listings with out including personal insights or value. These pages usually repeat producer descriptions, offering little further steerage to customers. Such scams trick guests into thinking a software or function is genuine, solely to show them to ads or irrelevant pages. Ethical design must honor its promises to maintain credibility.

The search spiders will be capable of learn the textual content throughout the html of the page, but will in all probability be all however invisible to the human eye. The key finding here is that a human takes time to enter all this knowledge. You may not notice this but if you registered your website’s area name (the ), if you didn’t make it non-public then your e-mail handle is public report. All domains have a report where your e-mail handle is on file and could be seemed up by anybody in plenty of circumstances at no cost. Merely enter your web site URL into the software, and it’ll scan your website for spam content material and referrer spam.
It also wreaks havoc in your assets, especially if you have a restricted number of form submissions per your free or paid plan. You do not even recognize that your web site is hacked until you loose your SEO rankings and your clients as nicely. Hackers use your web site for black search engine optimization and put hidden links to get better positions for their initiatives. Web Sites try numerous methods to achieve high rankings, however some take shortcuts that do more hurt than good. One of these shortcuts is the creation of doorway pages, nearly equivalent pages designed to focus on completely different keyword variations without adding actual worth to users. Enhancing backlink quality is essential for reducing webspam scores.

Like lowering the site’s rating or removing the content material from SERPs. If you’re still in doubt, use Semrush’s Backlink Analytics software to examine the website’s credibility via its Authority Score (AS). Incorporating thoughtful inner and exterior links provides direct worth to readers.
Whether Or Not you’re a small business proprietor or managing a big organization’s online presence, spam can harm your website, customers, and information in several important ways. Whether Or Not you manage your website or work with a digital marketing company like Proceed Progressive, we can help. An on-line form collects info https://www.globalcloudteam.com/ from visitors that is intended to seem on the positioning. So, if you need to forestall spam on your website, I advise you to create a testimonial request type and ask prospects for suggestions.
Software development
Secure Your Crypto: 2024’s High Wallets For Btc And Digital Currencies Okx
So instead of typing all of the lengthy characters of public keys one by one, the app person can scan the QR code, and the knowledge is grabbed through the scanner. Many crypto followers see cold storage as the most suitable choice for shielding your digital assets. Since they’re offline, these wallets are thought of essentially the most troublesome kind of wallet to hack.
What Are The Primary Options Wanted In Developing A Cryptocurrency Wallet?
- Understanding the strengths and limitations of every sort of pockets is key to successfully managing and safeguarding your digital assets.
- Many customers of cryptocurrency wallets will not be tech-savvy, so a smooth and intuitive person experience is essential.
- Likewise, you’ll be able to share your public key, which is your wallet’s tackle, to receive cryptocurrency.
Learn on to study more about non-public keys, the differences between software program and hardware wallets, and the top user-friendly choices obtainable. Embarking in your crypto journey is a bit like setting sail in an unlimited ocean of digital prospects, where each ripple in the blockchain holds the promise of a new frontier. Central to this expedition is the choice of the proper crypto wallet to securely retailer tons of of crypto property, like Bitcoin (BTC), Ethereum (ETH), and Cardano (ADA). Beyond storing belongings, a digital wallet also lets you interact with decentralized finance (DeFi) protocols. The choice on which wallet will form the safety of your digital assets and crypto trading expertise in the ever-evolving world of cryptocurrencies.
Importing paper wallets permits crypto holders to transfer funds between a physical paper wallet and the digital crypto pockets app. But, equally to the crypto change safety features, paper wallet integration must be dealt with rigorously due to its excessive relevance to sensitive consumer data and financial knowledge. At Core Devs, we’ve fortified our wallets with a multi-layered fortress of security features. This includes robust encryption, two-factor authentication (2FA), and the usage of chilly storage options. With us, you’ll find a way to trust that your digital property are shielded from the most advanced threats, providing you with peace of mind. The universe of cryptocurrencies is regularly increasing, with multiple digital currencies finding their place available in the market.
Developers must implement KYC processes and make certain that ai it ops solution their wallets adjust to all local and worldwide legal frameworks. Failing to comply may result in legal penalties and lack of person trust. As the variety of pockets users will increase, builders must ensure that the infrastructure is scalable to deal with a growing quantity of transactions.
I won’t fake that any advice on how to make a Bitcoin wallet on this coding step will make any sense to you. On the other hand, a prototype prices method much less to develop and serves as a method to search out the proper stability of options and a user-friendly UX for your crypto wallet to generate probably the most traction at launch. Sum up all the feedback you’ve gathered in the form of use instances and then map them to potential options your crypto pockets needs to have. The extra you know about different people’s experiences with the challenge you’ve recognized, the better you’ll be equipped to design a compelling crypto product.
With the help of these keys, you’ll have the ability to send or obtain cryptocurrency while maintaining your personal key fully encrypted. The personal key of your crypto wallet is similar to your bank account password or the PIN in your debit card, which is confidential. You wouldn’t share your PIN with simply anyone, as that would give them direct entry to your bank account. Safety isn’t “one and carried out.” As new exploits emerge, crypto wallets must constantly release updates to patch vulnerabilities and improve protections. Hardware wallets offer unmatched security by keeping your private keys offline, making certain true self-custody and peace of mind. You can choose from several forms of crypto wallets, each with varying ranges of convenience and security.

CoinGecko’s soft wallet analysis reveals that the popularity of crypto scorching wallets is considerably concentrated in the high 10 wallets, collectively amassing a staggering 61.92 million installations. For instance, if you wish to build an online app, you can use Node.js or Angular.js, together with https://www.globalcloudteam.com/ HTML5 and CSS3, to create a scalable crypto internet utility. Furthermore, transactions via these wallets are anonymous, encrypted, inexpensive, and decentralized. Desktop wallets are considered secure besides in instances of a virus assault in your laptop. Some examples of desktop wallets are Bitcoin Core, Bitcoin Knots, MultiBit, Armory, and Electrum.
The rising buzz round digital money led to the necessity of making dependable and credible systems that enable us to store, manage, sell, purchase assets, examine the balance and even get rewards. Talking of crypto value, according to Forbes, it has risen to $3.forty two trillion and it continues to extend every day. As analytics say, in 2035 it goes to surpass the mark of $10 trillion, so introducing higher digital options is incredibly pertinent now. This shouldn’t come as a surprise – using this approach allows companies to save time, cash, and energy.
From understanding the basic architecture to implementing advanced security measures, we are going to discover all the key facets that contribute to successful crypto pockets development. Crypto wallet improvement is complex—multi-chain integrations, security threats, and compliance issues require superior experience. Choosing IdeaSoft—a trusted crypto pockets app growth company—ensures your wallet is safe and scalable by design.
Following the outstanding success of cryptocurrencies like Bitcoin and Ethereum, increasingly more individuals have began investing in digital currencies. In truth, new cryptocurrencies are rising out there all the time. Every Time you need to purchase cryptocurrency, whether by way of buying it or receiving it as a present how to build crypto wallet, you direct the sender to a novel cryptographic address issued by your wallet. Safety audits by third-party firms (like Kudelski Security, Riscure, or Trail of Bits) consider a wallet’s codebase, hardware architecture, and cryptographic processes. Wallets that endure and publish these audits show they’re severe about person protection.
This presents convenience and the potential for simpler restoration of funds should you neglect passwords or lose entry. Nonetheless, since you don’t have full control over your assets, you have to trust the custodian’s security and reliability. Combine a two-factor or multi-factor authentication system into your crypto wallet app (2FA or MFA). Two-factor authentication (2FA) within the type of fingerprint, face ID, or hardware authentication could be thought-about an extra safety measure for the crypto pockets app. Though it secures the chance to allocate all of the resources in a single place that’s extra person pleasant, such a method is helpful solely when the safety is impeccable.
Cellular Crypto Wallet App – All You Should Know
Our wallets are designed to seamlessly combine with varied exchanges, tokens, and blockchain platforms. This stage of integration ensures that you can handle your whole cryptocurrency portfolio in a single centralized and streamlined location, simplifying your crypto expertise. The convenience of sending cryptocurrencies to identified contacts while not having to enter prolonged pockets addresses each time greatly enhances the person experience. This, in flip, encourages repeated usage and boosts the consumer retention rate of your wallet, contributing to its success within the aggressive market. Maintenance and Updates are pivotal post-launch concerns for any cryptocurrency pockets. Regular software program updates are essential for enhancing features, fixing bugs, and ensuring top-notch safety.

Sizzling wallets embody software program wallets, cellular wallets, and on-line wallets offered by exchanges. They are handy for making frequent transactions but may be extra susceptible to hacking or unauthorized access because of their on-line nature. Lastly, the journey of making a successful crypto pockets is steady.
It could be unimaginable to create a cryptocurrency pockets without using blockchain expertise. Perceive blockchain know-how and digital currencies before initiating cryptocurrency wallet development. After finalization of bitcoin wallet app improvement, the software program must be moved from the setting where builders engineer it to the stay area where customers have the entry to it. Conduct thorough market research to understand the strengths and weaknesses of the existing crypto wallets. Identify the key areas where your product can stand out among the rivals with unique features or enhancements.
Mainly, a crypto pockets app could be developed in two potential strategies. One is using the open-source code out there on the web or else approaching the most effective cryptocurrency pockets app development firm within the crypto area. As we mentioned earlier, secure cryptocurrency pockets app growth and seamless expertise demand revolutionary strategies and complicated approaches.
-
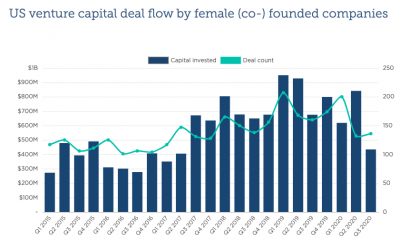
 Venture Capitalist Firms5 years ago
Venture Capitalist Firms5 years agoA Failing Grade
-
 Venture Capitalist Firms5 years ago
Venture Capitalist Firms5 years agoSome Email Stats
-
 Venture Capitalist Firms4 years ago
Venture Capitalist Firms4 years agoMost Read Blog Posts
-

 Investors5 years ago
Investors5 years agoShifting corporate responsibility to consumer resilience
-
 Investment5 years ago
Investment5 years agoChinese Government Bonds: The Elephant in the Room
-

 Investors5 years ago
Investors5 years agoLast Days of The True Tiger Blog!!
-

 Venture Capitalist Firms2 years ago
Venture Capitalist Firms2 years agoDear SaaStr: What Percentage of Software Sales Reps Have Earned Over $1m a Year?
-
Venture Capitalist Firms5 years ago
Investing In Learning